If you're delving into the world of cryptocurrencies, you've likely come across terms like "Hashing" and "SHA-256". In this piece, we'll explore the significance of SHA-256, a vital component of cryptocurrency security, especially Bitcoin. Without diving too deep into the mathematical underpinnings, we'll explain why it's the backbone of digital asset integrity.
The information contained here is for general information only. It should not be taken as constituting financial advice. Stormrake is not a financial adviser. You should consider seeking independent financial advice prior to making any personal investments.
Deciphering SHA-256 in the Cryptocurrency Space
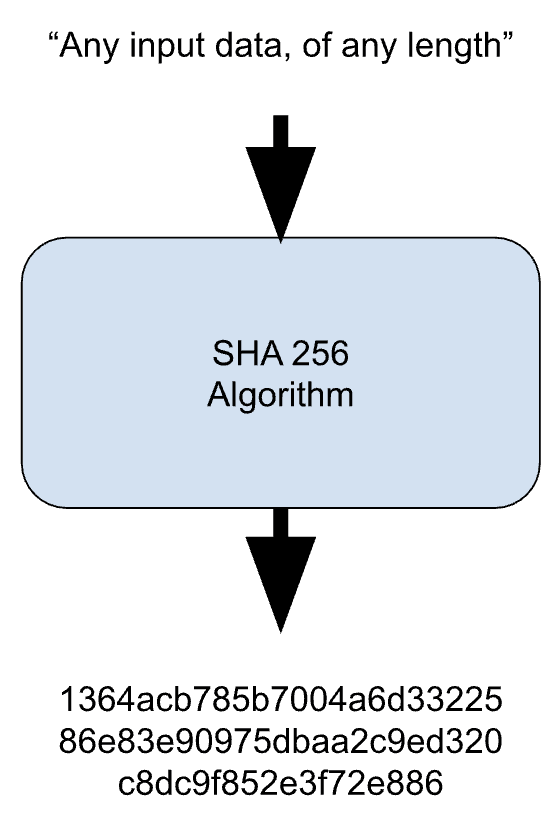
One-Way Street: SHA-256 and Data Security
Crucially, SHA-256 is a one-way function: you can generate a hash from input data, but you can't retrieve the original data from its hash. This feature is instrumental in safeguarding sensitive information like passwords, allowing only the hash to be stored. Even if a system breach occurs, the original password remains secure as hackers can't reverse-engineer it from the hash.
Collision Resistance and the "Birthday Paradox"
In the context of hashing, a "collision" occurs when two different inputs produce the same hash output. You might think such an occurrence would be rare given the vast number of possible hash values – 2^256 for SHA-256. However, the "birthday paradox" suggests that the chance of a collision becomes more likely than not after about 2^128 different messages have been hashed. But don't be alarmed – 2^128 is an astronomically large number, exceeding the estimated number of atoms in the observable universe.

SHA-256 in Bitcoin Network Security
Conclusion

Create a brokerage account today
If you enjoyed this Thunder Trading, feel free to open an account and gain access to more proprietary research and work with your very own dedicated crypto broker.
No Advice Warning
Disclaimer
All statements made in this newsletter are made in good faith and we believe they are accurate and reliable. Stormrake does not give any warranty as to the accuracy, reliability or completeness of information that is contained here, except insofar as any liability under statute cannot be excluded. Stormrake, its directors, employees and their representatives do not accept any liability for any error or omission in this newsletter or for any resulting loss or damage suffered by the recipient or any other person. Unless otherwise specified, copyright of information provided in this newsletter is owned by Stormrake. You may not alter or modify this information in any way, including the removal of this copyright notice.Copyright © 2022 Stormrake Pty Ltd, All rights reserved


